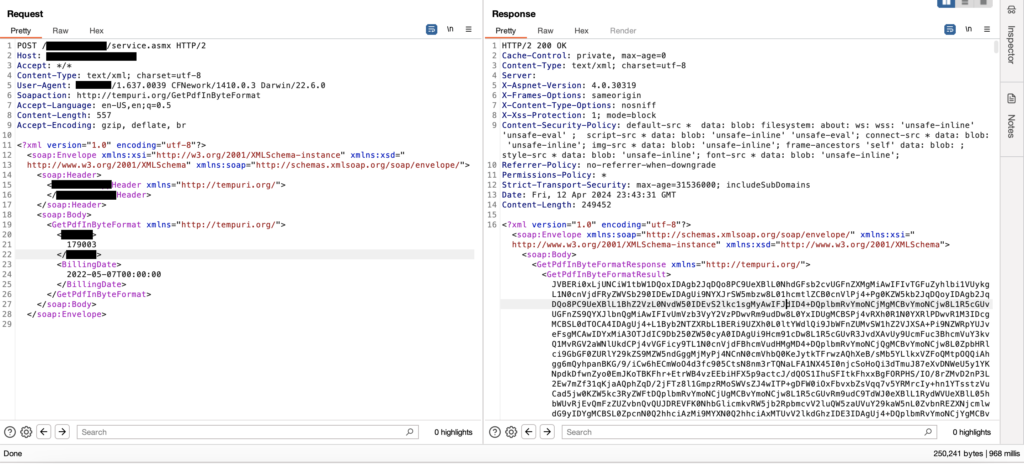
I was testing on a private program when I came across several endpoints that utilized a customer ID to retrieve information about that user’s account. I was going through each one testing for IDOR and not having any luck. The server was doing proper authorization checks and denying me access to other account’s data. I finally came across an endpoint that allowed customers to view their bills in a PDF format. The service was using Simple Object Access Protocol (SOAP), a network protocol for exchanging structured data between nodes using XML. Since this utilized XML my first thought was to see if it was vulnerable to XXE. Unfortunately, it was not. Since the requests were being sent with a user ID my next thought was to try IDOR. I removed all authentication values, sent the request and BOOM! I got a 200 response with the base64 encoded PDF of my bill – totally unauthenticated.
To view the encoded payload I created an HTML page with this simple iframe:
<iframe src="data:application/pdf;base64,ENCODED DATA HERE" height="100%" width="100%"></iframe>I then enumerated the user ID value and was able to view base64 encoded bills for other customers – again unauthenticated. These bills contained PII such as first and last name, phone number, home address, and mailing address. It also contained current and previous balances. Once I confirmed this I immediately stopped my testing and submitted the vulnerability. The organization confirmed my findings as critical severity and awarded a really nice bounty!
